Creating a strong posture against increasing cyber threats and challenges
From the increased migration to the public cloud to the emergence of prevalent threats like micro floods, application-layer DDoS attacks and ransom denial-of-service, 2021 presented organisations with an array of new security challenges and threats.
Although it’s only May, 2022 has presented a myriad of cyber challenges and threats. In the first few months of the year, the Australian Cyber Security Centre (ACSC) raised an alert for all Australian organisations to urgently adopt an enhanced cyber security posture. Following Russian-linked cyberattacks on the Ukraine, ACSC issued an urgent warning to local businesses and organisations to be on alert against heightened malicious activity from state-sponsored cyberattacks. Businesses and organisations globally needed and still need to ensure that their security infrastructure and posture remains heightened at all times.
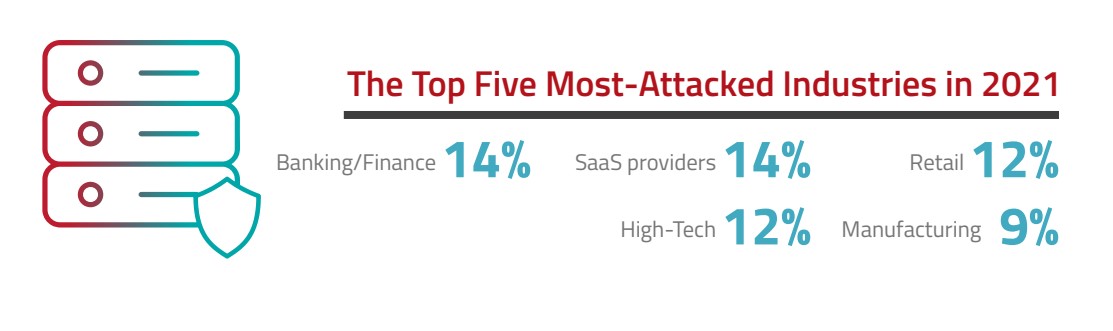
Closing the vulnerability gap
While organisations continue to elevate their security level, there are still major problems facing many industries, such as the Apache log4j vulnerability. This is a cybersecurity loophole exploiting a small piece of software that is used to record activities of various computer programs or used to log events or errors – and has the potential to give cyber criminals full control of a server.
The vulnerability leverages the Java Naming and Directory Interface (JNDI) service, which is a fundamental component of Java. While the log4j vulnerability itself was a new discovery, exploiting the JNDI service to conduct these types of deserialisation and injection attacks is not. Given a good amount of documentation and tools to perform JNDI based attacks already exists on the internet, it did not take long before in-the-wild scanning and exploit activity for Log4j specific vulnerabilities was detected.
The Apache Security team has come up with the advisory of CVE-2021-44228. Along with this bug, the Apache team has fixed a couple of more vulnerabilities in Log4j. You can check the description and mitigation/fix of the vulnerabilities. So we strongly recommend patching your application (server) before it gets in the hands of bad actors. Follow Apache guidelines to fix the vulnerabilities.
Increasing your security posture
As global events continue to evolve, one of the most significant threats for organisations is becoming collateral in a proxy war fought by patriotic hactivists. The threats and potential for cyber attacks that might follow as conflicts escalate and relationships deteriorate between nations or between online communities are very real.
Organisations across the globe should continue bolstering their cyber security resilience, now more than ever.

How Radware can help
Radware web application security solutions, specifically AppWall and Cloud WAF Services, detected and blocked Log4Shell exploit attacks through web application parameters and HTTP header fields within hours of the vulnerability being announced, typically as Server Side Request Forgeries.
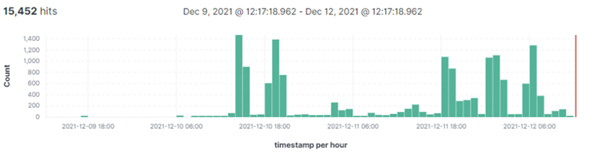
Between December 9, 6pm UTC and December 12, 12pm UTC (very soon after the vulnerability was announced), several thousands of exploit attempts were detected.
Cloud WAF Blocked Exploits (per hour)
Radware experts explain that as updates are made available, agencies must update software that uses Log4j to the newest version, which is the most effective and manageable long-term option. In parallel, organisations should implement mitigating measures at the first point of entry to stop an attack (and future zero-day attacks), such as a properly configured web application firewall (WAF).
As part of a holistic security framework, a WAF protects online applications delivered from a variety of application layer attacks. While properly configuring a WAF is notoriously difficult, Radware’s AppWall and Cloud WAF solutions automatically generate policies and leverage positive security models per application, to ensure very high levels of security with almost no manual intervention required.
Radware API Protection, a key component of Radware Cloud WAF, automatically maps and catalogues known and unknown application APIs. The solution parses all API traffic to and from each application, learning legitimate API schemas and traffic, and blocking attacks and malicious behaviour.
Radware’s WAF and API protection services provide a turnkey solution to help protect from even the most sophisticated, zero-day vulnerabilities on web applications, such as those that exploited Log4j.
Taking it a step further
Radware’s WAF and BOT Management: A critical combination
Over 50% of web traffic is comprised of bots, and 89% of organisations have suffered attacks against web applications.
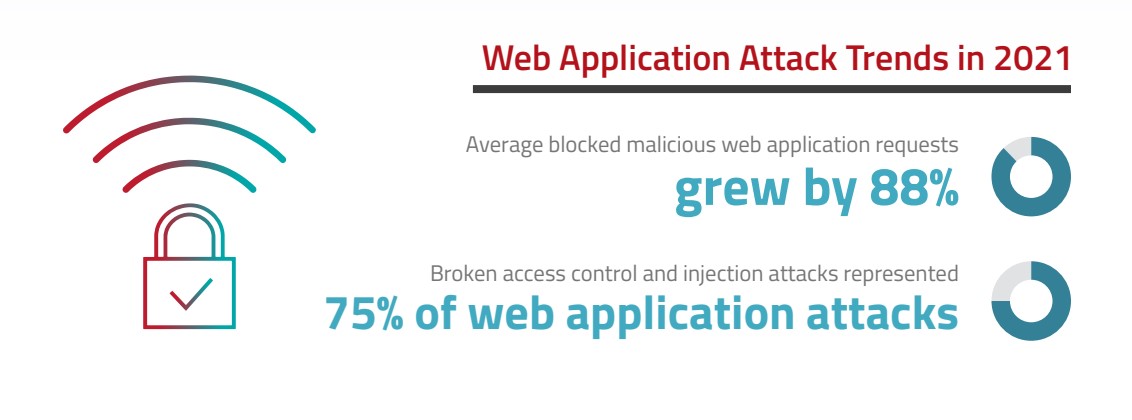
Web application firewalls are a cornerstone for safeguarding websites against application vulnerability exploitations like SQL injections, cross-site scripting (XSS), cross-site request forgery, server-side request forgery, session hijacking and other web assaults. When to it comes to bot management, WAFs typically come equipped with basic bot mitigation capabilities and can block bots based on IP addresses or device fingerprinting. However, when facing more advanced, generation 3 and generation 4 bots, these aforementioned capabilities fall short.
Bots target all channels: Websites, Mobile Apps, APIs

Protect your business from data theft, L7 DDoS attacks, denial of inventory, web scraping. 80% of organisations can’t distinguish good bots from malicious bots
Next-generation bots use sophisticated techniques to remain undetected, such as mimicking human behaviour, abusing open-source tools or generating multiple violations in different sessions. Against these sophisticated bot-based threats, organisations require a more comprehensive solution:
- Sophistication of attack detection techniques
- Ability to detect advanced human-like bots
- Robust threat research
- Intelligence to capture emerging bot trends
- Sophistication of attack prevention
- Detection accuracy and scalability
- Integration and interoperability
- Technology vision and roadmap
- API protection capabilities
Let Outcomex and Radware heighten your security posture
With Outcomex’s dedicated team of cyber security practitioners, we can help to deploy, manage, and monitor security portfolios, ensuring environments are alert to the latest threat profiles.
Get in touch with Outcomex and see how Radware and Outcomex can help you heighten your business’ security posture.




