Helping you build sound cyber resilience
Considered to be one of the most effective defence strategies against cyber criminals, Essential Eight is a prioritised list of core mitigation strategies developed by The Australian Cyber Security Centre (ACSC) with the sole purpose of helping organisations protect their systems against a range of attacks, making it much harder for adversaries to compromise systems.
Implementing the Essential Eight proactively can also be more cost-effective in terms of time, money and effort than having to respond to a large-scale cyber security incident. The strategy focuses on three key areas of cyber security:
- Preventing attacks
- Limiting the extent of attacks
- Mitigation strategies for data recovery and system availability
Strategies to prevent and limit the extent of cyber security attacks
By targeting the three key areas (preventing attacks, limiting the extent of attacks, and mitigation strategies for data recovery and system availability), the ACSC discovered that the Essential Eight mitigates about 85% of all targeted cyber-attacks. The Essential Eight cyber security controls fall within these broader categories:

Application Control
Prevents the execution of all non-approved applications (including malicious code), including .exe, DLL, scripts.

Patch Applications (Flash, Web Browsers, Java, etc.)
Security vulnerabilities in applications can be used to execute malicious code onto your systems. Be sure to patch/mitigate your computers with ‘extreme risk’ vulnerabilities and use the latest version of applications.

Configure Microsoft Office Macros Settings
Macros can be used to deliver and execute malicious codes. Configuring your macro settings will block macros from the internet and only allow vetted macros in ‘trusted locations’.

User Application Hardening
Flash, ads and Java are popular ways to deliver and execute malicious code. Configure your web browsers to block these on the internet and disable unneeded features in Microsoft Office and web browsers.

Restrict Administrative Privileges
Admin accounts are key to gaining full access to information, operating systems and applications. Regularly revalidate the need for privileges on different accounts, and restrict admin privileges based on user roles/duties.

Patch Operating Systems
Security vulnerabilities in operating systems can be used to further the compromise of systems. Patch/mitigate computers with ‘extreme risk’ vulnerabilities and use the latest operating system version.

Multi-Factor Authentication (MFA)
Stronger user authentication makes it harder for hackers to access sensitive information and systems. It is important to enable MFA so only the right users can access important data.

Daily Backups
To ensure information can be accessed following cyber security incidents, it is important to regularly back up new/changed data, software and configuration settings.
Maturity levels
The ASCS has defined four maturity levels that help organisations determine the maturity of their implementation of the Essential Eight. Maturity levels are based on preventing and combating increasing levels of cyber attacks (i.e., tools, tactics, techniques and procedures) and targeting. These maturity levels outline what is likely to be compromised and what should be addressed:
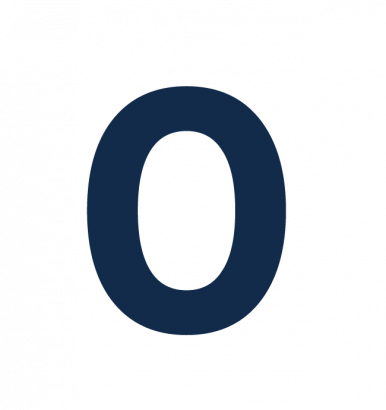
Maturity Level 0
Signifies that there are weaknesses in an organisation’s overall cyber security posture. When exploited, these weaknesses could facilitate the compromise of the confidentiality of their data, or the integrity or availability of their systems and data.

Maturity Level 1
Common weaknesses in multiple targets are exposed by cyber criminals, mostly by using common social engineering techniques to tricks users into weakening the security of a system and launching malicious apps.

Maturity Level 2
Attacks are more targeted, where cyber criminals use advanced tools and tactics to bypass security controls. This includes actively targeting credentials using phishing and employing technical and social engineering techniques to circumvent weak MFA.

Maturity Level 3
The sophistication of this attack is higher – weaknesses are exploited in an organisation’s security posture where cyber criminals concentrate on particular targets and are willing to invest time and effort into bypassing particular policies and controls, evading detection (i.e. covering their tracks) and solidifying their presence.
Evaluating the effectiveness of your Essential 8 controls
The best way to evaluate the effectiveness of your Essential 8 controls within your organisation is to do an Essential 8 Online Executive Assessment. By doing this, you’ll better understand the areas where security vulnerability and weaknesses are, allowing you to make improvements and strengthen these areas. The Essential 8 Executive Assessment will only take a few minutes to complete.
Need help implementing the Essential Eight or understanding your organisation’s maturity level?

Our team of cyber security experts can help you understand the current maturity level of your organisation, including the effectiveness of the controls you have in place. We can assist in implementing and/or maintaining the Essential 8 security controls, helping you protect your systems against a range of attacks, making it much harder for adversaries to compromise systems.
