Data breaches are putting Australian businesses in the news for all the wrong reasons and leading to record financial losses.
Organisations are ready to invest to protect their data, but need to do it wisely to match evolving threats.
A taste of recent high-profile breaches
- A popular online graphic design tool suffered a monumental data breach impacting 137 million users – usernames, real names, email addresses, encrypted passwords and partial payment data stolen.
- A high-profile telco internal network breach – compromising personal information impacting up to 9.8 million customers, including names, birth dates, addresses, phone numbers, passports and driver’s licence numbers.
- A university and a sophisticated spear-phishing attack – infiltrating personal information dating as far back as 19 years.
- A prominent government agency staff email hacked – accessing 5 million documents, 10% of which contained sensitive data.
- A hospital unit fell and a sophisticated ransomware attack – impacting 15,000 patient files including personal information and sensitive medical data.

What types of human behaviour put your business at risk?
According to a study by IBM, 95% of cyber-security breaches result from human error. Yet, organisations regularly fail to prioritise human factor cybersecurity and ignore behaviours like:
- weak passwords
- storing passwords incorrectly (sticky note, anyone?)
- outdated or unsecure software
- careless data handling
- failing to recognise Business Email Compromise attacks such as phishing
- unauthorised access to company devices.

Minimise breaches caused by human error
- Implement ongoing cybersecurity education and training programs
- Install access controls, ensuring users only have access to data and functionality needed to perform their roles
- Practise good password hygiene by implementing an advanced password management policy and using multi-factor authentication
- Encouraging a culture of open discussion, question asking and collaboration around cybersecurity
- Visible daily reminders encouraging users to be mindful of cybersecurity
Employees don’t have to be your weakest security link. According to Cisco’s Senior Vice President, Chief Information Security Officer Steve Martino, “with the right knowledge, understanding and encouragement, employees can and will be the best line of cyber defence you’ll ever have.”
Limiting the damage with internal encryption
Despite the best laid plans, tech and education, breaches still happen. Limit the damage with encryption.
Encryption is the process of converting or scrambling data into an unreadable, encoded version that can only be read with authorised access. Ideally, encryption prevents interception of sensitive data in the first place. But it will limit the damage by making the data unreadable and useless to threat actors.

Two types of commonly used encryption algorithms
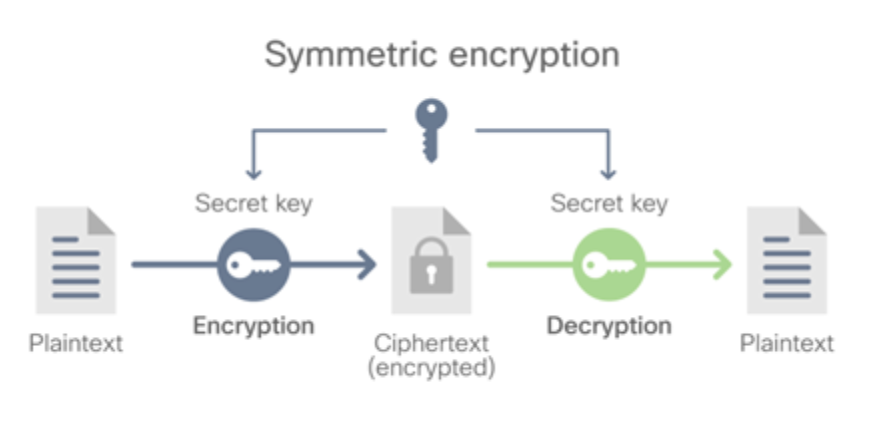
- Symmetric encryption (also called shared key algorithm) which uses the same key for encryption and decryption. Because it uses the same key, symmetric encryption can be more cost effective for the security it provides. That said, it is important to invest more in securely storing data when using symmetric encryption.
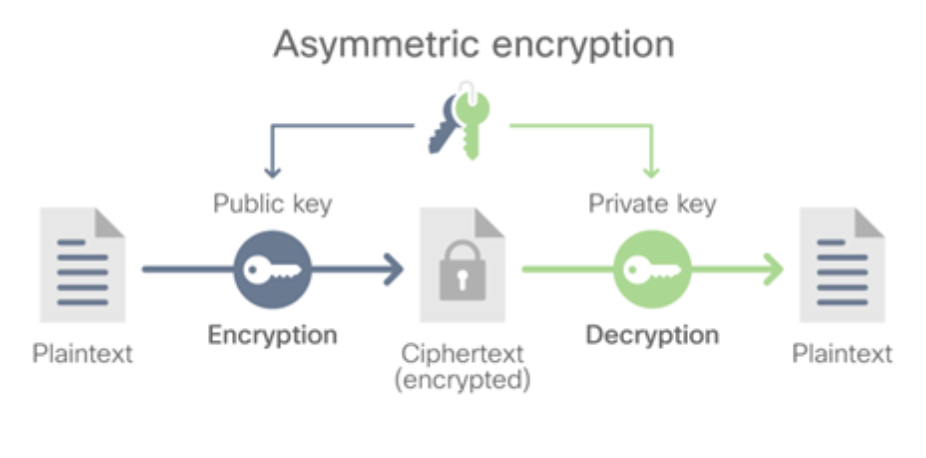
- Asymmetric encryption (also known as public key algorithm) which uses two separate keys: a public key and a private key. Often a public key is used to encrypt the data while a private key is required to decrypt the data. The private key is only given to users with authorised access. As a result, asymmetric encryption can be more effective, but it is also more costly.
Leveraging the latest cyber-security technology
Outcomex partners with Cisco to provide a range of solutions with flexible licence options:
- Cisco Umbrella – use the Internet’s infrastructure to enforce security and block malicious activity before a connection is ever established.
- Cisco SecureX – expand your threat detection and response capabilities using automation and remediation features.
- Cisco Secure Endpoint – stop threats before they cause compromise with powerful detection and response capabilities.
Additionally, Outcomex can help strengthen your security posture by providing a full-scale evaluation of your security processes, systems and infrastructure, and identify possible vulnerabilities and areas of weakness. Through our end-to-end security offerings, we can help your business reduce gaps in security, creating optimal defence framework and security strategies.
Why choose Cisco and Outcomex to prevent data breaches
During uncertain economic times, look to invest your cyber-security dollars with a proven partner. As Cisco’s Larry Scherzer writes, “For many businesses, cyber security can be a significant expense that comes up for review often, even when there is no threat of a recession.”
Whether you’re implementing new products and services, or creating new channels of engagement, if you have a digital presence then ensuring your business remains secure is key.
Undergoing an end-to-end security assessment is essential for ensuring the security and integrity of any system to help prevent data breaches, system downtime, and other costly security incidents, ultimately protecting the organisation’s reputation and bottom line. See our end-to-end cyber security services here.
Strengthen your cyber-security armour by reaching out to us today.




