Vulnerability management shouldn’t feel impossible.
Most organisations understand the importance of staying ahead of vulnerabilities—but the reality is rarely straightforward.
Elliette Wireframe Kit
A dark themed wireframe kit made of interchangeable components to speed up your next project.
With Outcomex, you gain measurable security outcomes:
Expert analysts
Round-the-Clock Support
ISO 27001 Certified
Organisations we have helped protect:
Scalable solutions tailored for your organization
Take the burden of vulnerability management off your team and start closing your security gaps today.
Essential
Comprehensive vulnerability scanning and reporting to cover your core assests.
- Industry-Leading Tenable VM Licensing
- Actionalbe Monthly Security Intelligence
- COntinuous Monitoring & Weekly Updates
- End-to-end Platform Management
- Dedicated Expert Support
- Seamless Onboarding & Rapid Deployment
- Strategic Security Reviews
Advantage
Expanded visibility and compliance reporting for a holistic security overview.
- Includes all Essential features, plus advanced capabilities
- Unified Security posture with Tenable One
- Expanded Threat Visibility (Identity, Web App, Attack Surface)
- Streamlined Compliance Reporting (Biannual)
Lifecycle Remediation
Proactive vulnerability resolution and strategic patch management to security gaps and strengthen your defenses.
- Proactive Remediation
- Strategic Patch Management
- End-to-end Vulnerability Lifecycle Management
Add-On Serivces
Enhance you security posture with our specialized serivce and mobules
- Tenate OT Security
- Tenable Cloud Security Posture Management
- Armis
- Penetration Testing
- Dark Web Monitoring
- On-demand Compliance
- Red Teaming
of breaches were due to a known unpatched vulnerability.20% eo beaches began with a vulnerability exploit.
is the average time to patch internet-facing assets. More than half are still unpatched after 32 days.
saw a 31% rise in disclosed vulnerabilities and 20% more active exploitations.
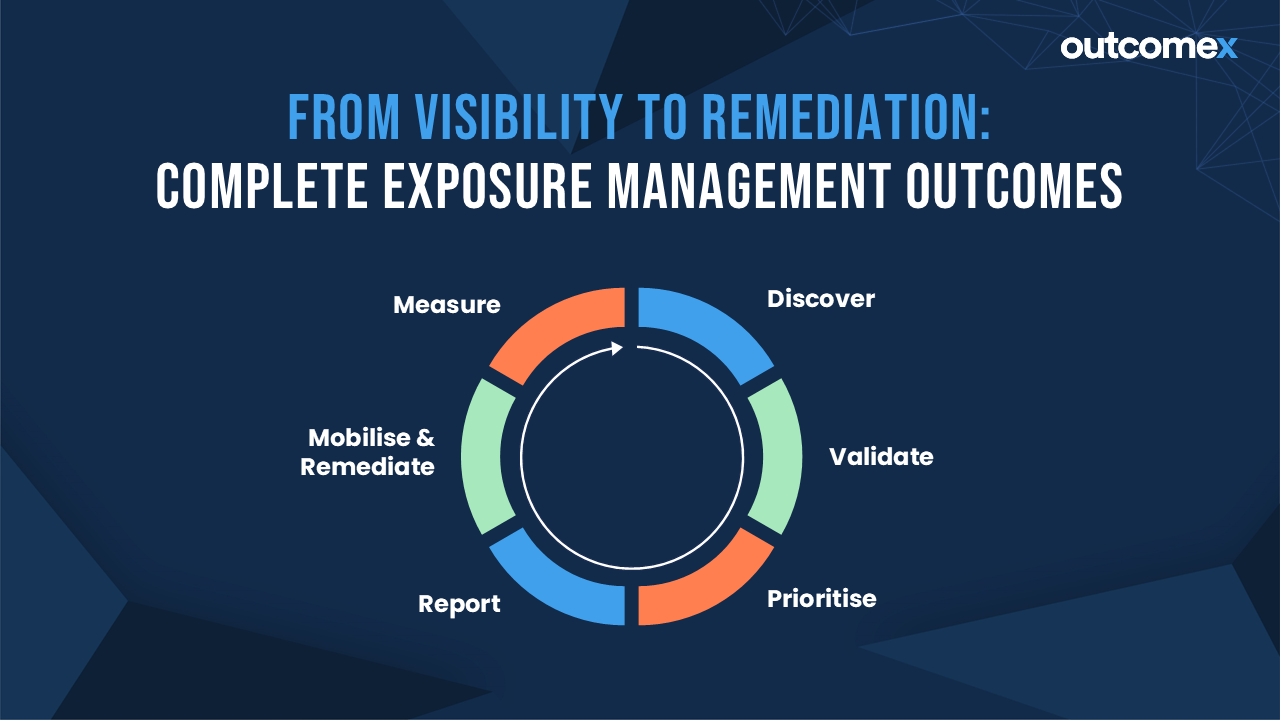
With our service, you will:
Your Trusted Partner in Cybersecurity
At Outcomex, cybersecurity is not just a service – it’s a commitment to protecting what matters most. With the increasing complexity of digital infrastructure and the growing sophistication of AI-driven threats, vulnerabilities can be exploited in minutes, but identifying and fixing them can take weeks.
This is where our Vulnerability Management Service steps in. With extensive experience and a proven history of success in securing diverse environments, our certified cybersecurity engineers use industry-leading tools and frameworks to detect, analyse, and prioritise vulnerabilities across your entire ecosystem, from on-prem systems to cloud platform.
Expert analysts
With Industry best certifications OSCP, GPEN, GWAPT, CEH and more.
Round-the-Clock Support
24/7 support for Scheduling, Monitoring, Analysis & Reporting of scanning activities.
ISO 27001 Certified
Demonstrating our commitment to maintaining high-security standards.
Certified Cybersecurity Professionals
Our team comprises experts with extensive experience in vulnerability management.
Tailored Solutions
We customise our services to align with your organisation’s specific needs and objectives.
Proven Track Record
Our success is reflected in numerous industry awards and recognitions.
Your Trusted Partner in Cybersecurity
At Outcomex, cybersecurity is not just a service – it’s a commitment to protecting what matters most. With the increasing complexity of digital infrastructure and the growing sophistication of AI-driven threats, vulnerabilities can be exploited in minutes, but identifying and fixing them can take weeks.
This is where our Vulnerability Management Service steps in. With extensive experience and a proven history of success in securing diverse environments, our certified cybersecurity engineers use industry-leading tools and frameworks to detect, analyse, and prioritise vulnerabilities across your entire ecosystem, from on-prem systems to cloud platform.
Expert analysts
With Industry best certifications OSCP, GPEN, GWAPT, CEH and more.
Round-the-Clock Support
24/7 support for Scheduling, Monitoring, Analysis & Reporting of scanning activities.
ISO 27001 Certified
Demonstrating our commitment to maintaining high-security standards.
Certified Cybersecurity Professionals
Our team comprises experts with extensive experience in vulnerability management.
Tailored Solutions
We customise our services to align with your organisation’s specific needs and objectives.
Proven Track Record
Our success is reflected in numerous industry awards and recognitions.
How we differentiate from other VM services
| Typical Vendors (The Old Way) | Outcomex (The Better Way) | |
|---|---|---|
| Scanning Frequency | Periodic, often quarterly or ad-hoc scans that quickly become outdated. |
Continuous and proactive scanning to detect new threats as they emerge, providing a real-time view of your risk. We meet E8 frequencies. |
| Reporting | Delivers overwhelming, raw data reports with thousands of vulnerabilities and little context. |
Provides risk-based, prioritised reports that focus on what matters most. We filter out the noise so we or you can fix the critical issues first. |
| Focus | Problem-finding. The service identifies vulnerabilities and leaves the hard work of fixing them to you. |
Problem-solving. We go beyond discovery to actively manage the entire lifecycle, from identification, remediation and verification of the fix. |
| Business Context | Treats all assets and vulnerabilities as equal, creating unnecessary work for your team. |
Aligns with your business by identifying critical assets and prioritising threats that pose a genuine risk to your operations. |
| Remediation | Puts the burden of patching and configuration changes entirely on your internal teams. |
Offers end-to-end remediation and support, providing clear guidance, assisting with patching, and validating that vulnerabilities are truly fixed. |
| The Outcome | A long to-do list, alert fatigue, and a false sense of security. |
A measurably stronger security posture, reduced risk, and an empowered IT team that can focus on strategic initiatives. |
Vulnerability Management as a Service FAQs
The main purpose is to ensure that all systems and software are up to date with the latest The main purpose is to ensure that all systems and software are up to date with the latest security patches, to identify and remediate any other vulnerabilities that may exist, and to prevent future vulnerabilities from occurring. patches, to identify and remediate any other vulnerabilities that may exist, and to prevent future vulnerabilities from occurring.
VMaaS is a comprehensive, ongoing service where we handle the entire lifecycle of managing your organisation’s security weaknesses. It goes far beyond just scanning. Our experts continuously identify vulnerabilities across your network, servers, and applications, prioritise them based on the actual risk they pose to your business, and provide expert guidance and support to remediate them before they can be exploited.
Your IT environment and the threat landscape are constantly changing. New devices are added, software is updated, and cybercriminals discover new attack methods daily. A one-off scan is just a snapshot that becomes outdated the next day. A continuous service ensures you are always aware of new risks, providing consistent and proactive protection, not just a point-in-time report.
Firewalls and antivirus are essential, but they are only two layers of security. A firewall protects the perimeter of your network, and antivirus software targets known malicious files. Vulnerability management addresses a different problem: the underlying weaknesses in your software and system configurations that an attacker could use to bypass your other defences. It’s a critical part of a “defence-in-depth” security strategy.
Not all vulnerabilities are created equal. We use a risk-based approach that goes beyond just the technical severity score (CVSS). We combine this score with other critical factors, including:
- Asset Criticality: How important is the affected system to your business operations?
- Threat Intelligence: Is this vulnerability being actively exploited by attackers in the wild right now?
- Exploitability: How easy is it for an attacker to leverage this weakness?
This allows us to focus your resources on fixing the issues that pose the greatest, most immediate threat to your business.
Absolutely. This is a key part of our “as a service” model. We don’t just hand you a list of problems. We provide clear, actionable remediation plans, work with your IT team to coordinate patching and configuration changes, and then re-scan to validate that the vulnerability has been successfully closed.





