Ransomware and cyberattacks need to move across an organisation to be successful. Preventing a breach is nearly impossible. The key is to keep ransomware and cybercriminals from moving through your network and getting to your most important digital assets. Microsegmentation stops attacks from moving by delivering intelligent visibility, creating an environment of Zero Trust.
Zero Trust architecture

Automated security enforcement
Automate the journey to Zero Trust segmentation by immediately enforcing selected policies or choosing to progressively enforce policies across the entire organisation.

Real-time application insights
Accelerate the move to Zero Trust segmentation by simplifying how to visualise and gain insights from all application communications. This visibility makes it even easier to create, enforce and test security policy across network, security and DevOps teams without breaking business-critical applications.

Multi-cloud security at scale
Easily and continuously enforce workload security at massive scale with any cloud or data centre. Embrace the cloud with confidence by leveraging unmatched insights, prioritise efforts and enforce security policies for any cloud application.
Microsegmentation
Gone are the days when a hard security perimeter was enough to protect critical assets and applications. A modern compute estate can span one or multiple data centres and public clouds, from hosted environments to partner networks. This inevitably broadens your attack surface and leaves ample opportunity for breaches, making prevention extremely difficult, if not impossible. Containment is paramount.
Microsegmentation plays a key role in achieving Zero Trust security. Microsegmentation has emerged as one of the best techniques to protect organisations against breaches by restricting attacker lateral movement and reducing your attack surface. Effective microsegmentation and Zero Trust implementation can provide the following ransomware containment advantages.
- Gain risk-based visibility. Capture critical insights in as little as an hour by automatically mapping all communications across your applications, devices and the cloud.
- Assess your vulnerabilities. Improve your digital defences and limit your breach exposure by pinpointing the applications and systems that are most at risk.
- Take action to contain ransomware. Contain ransomware and other cyberattacks proactively and during an incident by blocking unsafe communications and integrating Illumio data into SecOps.
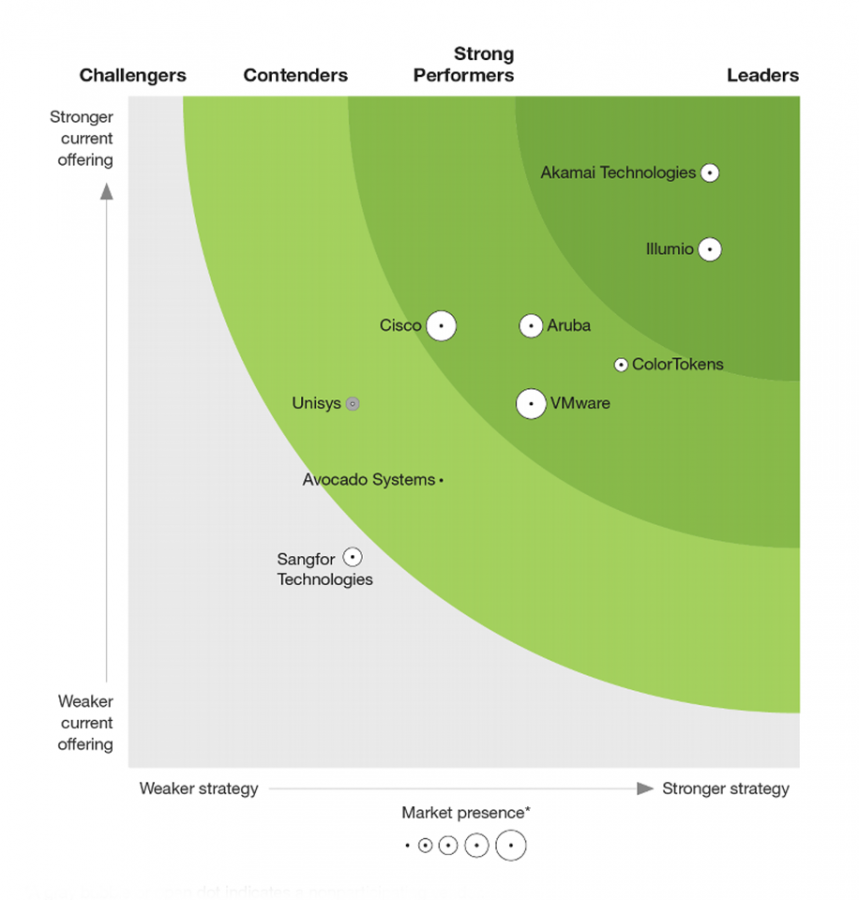
Market-leading Zero Trust solutions with Outcomex
Outcomex works with a variety of strategic security partners to provide Zero Trust solutions for clients, in addition to our wider cyber security solutions. This means selecting cutting-edge capabilities from the technology landscape, and one of those providers is Illumio.
Forrester named Illumio a Leader in The Forrester Wave: Zero Trust eXtended Ecosystem Platform Providers, Q3 2020 report, with the highest scores in the three primary categories: current offering, strategy and market presence.
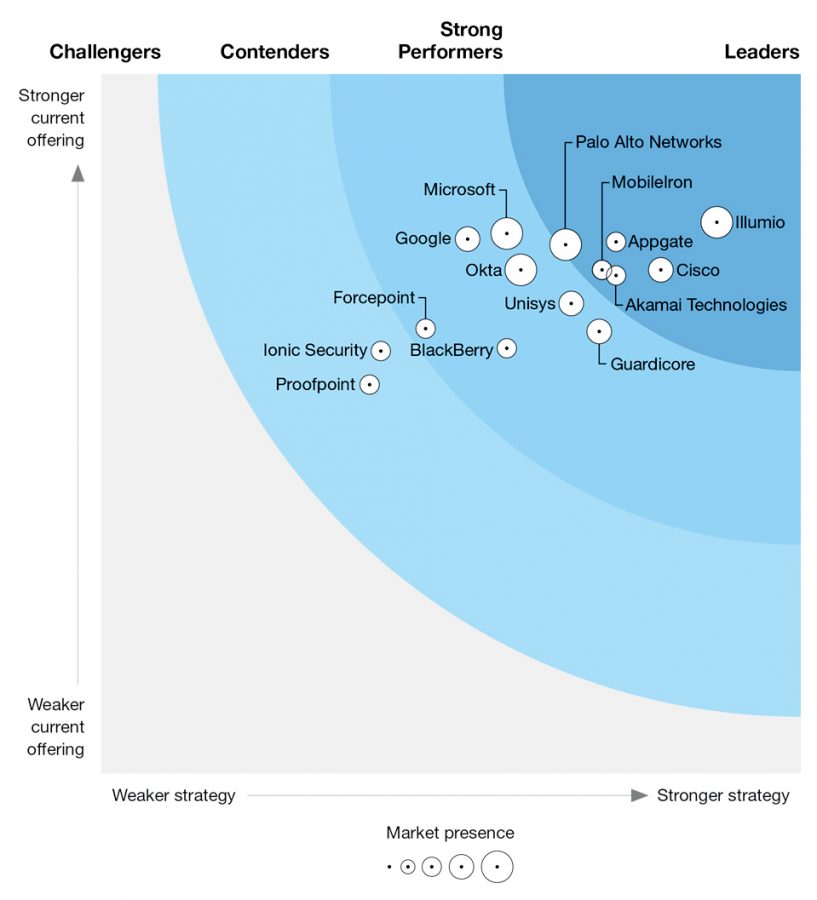
Workload security
Segment in minutes on your path to Zero Trust. Illumio Core is an easy, fast, and proven microsegmentation solution that stops attacks from moving by delivering intelligent visibility, a radically simple policy creation engine, and automated segmentation and enforcement.
Endpoint security
Extend Zero Trust to your endpoints. Illumio Edge contains ransomware and malware to a single endpoint – even if it hasn’t been detected yet.
Cloud security
Illumio CloudSecure provides cloud-native security made easy. Benefit from agentless, real-time visibility to understand your security risks and orchestrate cloud workload policies across hybrid and multi-cloud. Gain unmatched insights, prioritise efforts and enforce security policies for any cloud application.
Download “Secure Beyond Breach” to learn more
Download the “Secure Beyond Breach” eBook from Illumio to learn more about building a defence-in-depth cyber security strategy through microsegmentation.

